Automating Deployment of Enterprise Network with MPLS VPN Using Ansible
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 2680 words | ✅ Published: 18 May 2020 |
Introduction:
Multiprotocol Label Switching (MPLS) technology made its way in the field of computer networks in the mid-90s. IP routing is not being replaced by MPLS instead it works along with various routing protocols. MPLS permits data packets to be forwarded at the data-link layer, the switching layer, instead of routing through to layer 3, the routing layer. Hence, it is defined as functioning at Layer 2.5.
It a technique developed with an aim of better, efficient, and timesaving substitute to conventional IP routing, which expects each router in the network to individually determine a data packet’s next hop by examining the destination IP address before referring its routing table. This practice is not just tedious but also consumes hardware, possibly causing the network to perform poorly for applications such as VoIP, web conferencing, etc. MPLS is a routing technique proposed to speed up and manipulate traffic flow throughout enterprise and service provider networks.
Increase in both, the number of Internet users and the bandwidth requirements have put growing requests on the Internet service providers’ (ISPs’) networks. To meet this increasing demand for bandwidth, ISPs requires improved implementation and execution of switching and routing products. In addition to quicker convergence, the networks must deal with the multiplication of nodes, added routes in routing tables, additional streams in transit through a given point, and onwards. Overall, the need of the network providers is thus concerned with scalability, which is described roughly as the capability to extend the network in all these scopes exclusive of some tricky problem. Label switching has been in part driven by the necessity for scalability.
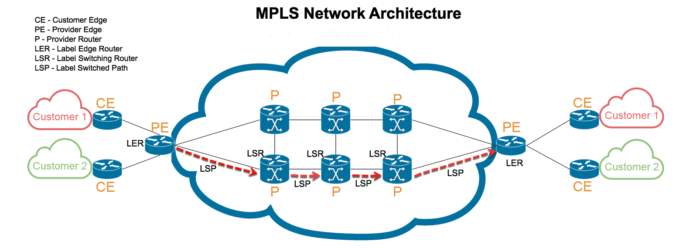
Fig 1: MPLS Network
Source: http://www.technologiesclusters.com/technology/wondering-how-a-multi-protocol-label-switching-works.html
In a nutshell, MPLS uses a label to determine which path to select to reach the destination. A label is attached to a packet when it enters at an ingress router or Provider edge router (PE) and it is called a PUSH. As the packet moves forward along the predetermined label switched path (LSP), the label is SWAPped at each router based on the forwarding decision. When the packet is received by the Egress router (provider edge router PE close to destination) the label is removed, this is called POP and the packet is then identified by the IP header.
Virtual Private Network (VPN) is a secure connection between two networks over the public network, Internet and delivers private services over a public network. All full mesh of tunnels is created to deploy VPNs. As the network scales and new devices get added it begins to grow difficult to maintain these types of tunnels as it requires reconfigurations of all edge devices in the VPN. While MPLS VPN is built on the peer model and is created in layer 2 and layer 3.

Fig 3: Types of MPLS VPN models.
The peer model allows the exchange of layer 3 information between the ISP and the customer. This is achieved without any interface or involvement of the customer and thus MPLS VPN is hassle-free, effortless and undemanding to maintain. It is easy to scale this type of a VPN as only the ISP edge devices require reconfiguration. MPLS L3 VPN uses private IP addresses instead of public IPs to connect and share the information.
“Network automation is the process of automating the configuration, management, testing, deployment, and operations of physical and virtual devices within a network”. [8] One of the primary reasons for automation in the field of networking is the growth of the IT sector and expensive network operations. The evolution and progress of stats and devices are beginning to outperform IT abilities, making conventional approaches almost impossible to deploy and maintain the operations smooth. In spite of that, up to 95 percent of modifications in a network are implemented manually, causing the functioning expenses 2 to 3 times beyond the expense of the network. For the business to survive and keep pace in the ever-growing digital world it is important to improve and increase the speed of IT automation.
Network automation helps in automating routine network errands and functions, with help of hardware and software solutions. Organizations look forward to network automation as it helps them control and manage monotonous and recurring procedures in order to enhance network service availability. Automation and orchestration when combined make network operations easier involving tangled configurations, devices’ management, traffic monitoring, etc., at the same time offering agility to adjust to a dynamic environment. Automation as completing repetitive tasks without human interference, and orchestration as the practice of looping together a sequence of such tasks to finish a process.
With the increase in media traffic in the form of video, social media messages, images, local machine applications, documents and more, the rapid expansion of network infrastructure is crucial. Network automation is seen as a possible solution to this problem. With decreasing costs of computational devices, is resulting in reduced computation cost. Virtual computing is also becoming popular pushing users to do their computation on the servers than buying these costly machines. Given these two reasons, network automation would be easily available and affordable for business in the coming years.
Ansible operates on the concept of decentralized agentless architecture. Ansible establishes a connection with nodes and pushes small codes, called “Ansible Modules” to them. Ansible executes these modules over SSH by default, and once finished these modules are than deleted. SSH is used as its transport protocol to operate its push model (but could also be operated in pull model). It is developed using python and supports templating using Jinja. Earlier ansibles ran ad hoc commands on servers but with tasks that need to be applied multiple times without anything major changing, they are now commonly running on target systems. Running of task multiple times has also been referred to as “playbooks”, which could be written in the standard of ansible derived YAML format.
Zabbix is an open-source software used to monitor servers, networks, and applications for their health and performance. It offers monitoring metrics, like network consumption, load and disk utilization of the CPU. It provides monitoring on a wide range of operating systems like Linux, Hewlett Packard Unix (HP-UX), Mac OS X, Solaris, and other operating systems but, to use it on Windows it has to be used through agents. One important feature of Zabbix is it can be implemented for agent-based and agentless monitoring. Agent-based monitoring is used on windows OS where agents are installed on to inspect functioning and gather data. This agent conveys the gathered data to a centralized Zabbix management server, and this information is then incorporated in reports in the Zabbix GUI. If detected any issues while monitoring, it alerts the user with notification. Similar actions are performed when monitoring is agentless, but it uses existing assets in a system to match an agent.
Literature Review
Enterprise networks have been deployed with multiple branches connected via ISP provider with the internet provider. Internet access to this is provided with MPLS VPN connectivity (Reshma et al. 2018). Reshma et al. 2018 also introduced secure connections from different customers to ISP using MPLS-based VPN, MPLS L3 VPN using VRG and MP-BGP. The model contained 10 routers, which were manually configured, which was a major reason for other work to become more popular than Reshma et al. 2018. [3]
The other part of work that closely aligns with this introduced to a system that automated VPN configuration and maintains a large-scale VPN deployment (Samll et al. 2015). Peer discovery and routing protocol introduced in Samll et al. 2005 advertises prefixes which help in removing static configurations and reducing costs for maintenance. These prefixes are also broadcasted along with different links which allow the peers to choose a route with a minimum metric, to support multi-home and mobile enclaves. This protocol has seen to scale up in GIG to over a thousand VPN gateways. [5]
DiffServ, MPLS, and dynamic resource allocation techniques were combined for a system that supports the quality of service over VPNs, called QoS-enables-VPN (Jia, Yuxiao, et al.) using dynamic resource allocation with an assumption that static behaviors could be described through /spl alpha/-stable long-range dependent stochastic process. In this work, the authors also investigate scenarios in which service providers establish service level agreement with the customer in cases where resources and QoS requirements are defined. Jia, Yuxiao, et al. extended the work to provide provisioning and management of QoS-enabled-VPNs. The improvement to earlier work uses integrated architecture which is implements at ISP’s infrastructure to combine the technologies combined in (Jia, Yuxiao, et al.) with dynamic resource allocation as it offers a higher degree of effectiveness in managing all available resources. Leading it to be more successful for increased business. [6]
One issue with these systems is the time-consuming configurations. The outcomes provide better performance of the system but at the cost of longer time to deploy them in a real-time environment where the changes are being made constantly. The proposed system will make the deployment of configurations as easy as just one click. With the help of pre-built modules in Ansible, the configuration will be pushed on the devices in minimum time. Also, the system proposes configuration can be done remotely, the administrator does not need to be physically present at the location of the device. The proposed system also aims at detecting discrepancies in the network with the help of Ansible modules integrated with Zabbix monitoring server making the network easy to troubleshoot.
Proposed system
In the proposed system, the connectivity between two customer sites is provided through the ISP. These customer sites will have the service of MPLS Layer 3 VPN connectivity. MPLS Layer 3 VPN connectivity is provided using private IP addresses. The proposed system is implemented by with two ISP providers connecting two customer sites, but one of the ISP provides a connection over MPLS L3 VPN service to the customer and the other ISP provides a normal connection with MPLS running in its core, this provides redundancy. The goal of this proposal is to provide a working model of an enterprise network with MPLS L3 VPN automated using Ansible. This project is deployed on GNS3 simulator using Ansible playbooks to automate the configuration process over an enterprise network. This proposal also aims at deploying a monitoring server to keep a tab of the network health during the traffic flow.
Future Work
As the project progress, this proposal would test its working with various network automation tools like Netmiko and Peramiko while making use of Cumulus Linux network operating system. As a part of future work, this project will also test its feasibility and functioning over AWS VPC. Also, using Napalm module the proposal will deliver discrepancies detection and other event-triggered detections.
Methodology
Topology:
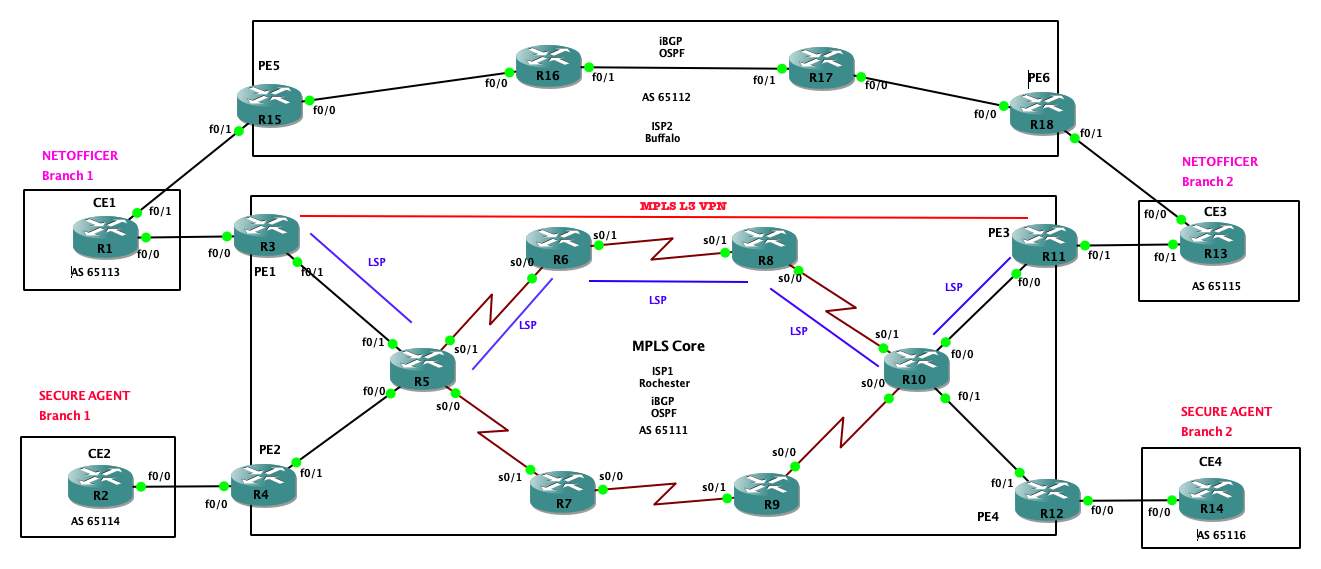
Configuration
In the proposed system, there are 2 ISPs, ISP1 and ISP2 that provide a connection between branches of these 2 companies NETOFFICER and SECUREAGENT.
ISP1 (Rochester):
- ISP1 is configured as an Autonomous system 65111.
- Routers R5, R6, R7, R8, R9, and R10 are core ISP routers, configured to run IGP (OSPF), MPLS to deploy MPLS L3VPN, iBGP
- R3, R4, R11, and R12 are provider edge (PE) routers, they provide a connection between customer CE routers and Core ISP routers. These routers will be configured to run iBGP, MPLS, MPLS VPN, MP-BGP, OSPF.
- When deploying MPLS network, OSPF is used as IGP but then again not for routing traffic. It is deployed to deliver routing for the core network to facilitate labels generation. MPLS makes use of Label Distribution Protocol (LSP) to advertise the labels to neighboring routers.
- All the routers in the core MPLS network are called Label Switched Routers (LSR) as they are responsible for adding, swapping, and removing labels from the packets and these routers are in the path of Label Switched Path (LSP).
- MPLS L3 VPN will be deployed between PE1 and PE3 to provide secure connectivity between CE1 and CE3.
- Multiprotocol BGP(MP-BGP) is an expansion of BGP protocol. While regular BGP supports IPv4 unicast address family, MP-BGP supports IPv4 and IPv6 unicast and multicast address families. Since the PE routers are configured to deploy MPLS VPN, MP-BGP is used to exchange IPv4 unicast to VPN tunnel over the node.
- Virtual Routing and Forwarding (VRF) is a key element of MPLS L3 VPNs. It makes a single PE router give the impression to be more than one to the customer edge (CE) routers. The PE router maintains independent and discrete routing tables for each customer. Each PE creates these distinctive routing tables with the help of their routing table methods for all the customers connected to the PE. This distinctive partition or isolation of routing tables lets PE routers to save routes and forward packets albeit the clients are exercising identical addressing scheme.
ISP2 (Buffalo):
- ISP1 is configured as an Autonomous system 65112.
- Routers R15, R16, R17, and R18 are core ISP routers, configured to run IGP (OSPF), MPLS to deploy MPLS L3VPN, iBGP, VRF.
- ISP2 is placed to provide redundancy. In case of an outage on ISP1, ISP2 will kick in and maintain the connectivity.
Ansible Server
- An ansible server over the cloud will be deployed to establish a connection with the nodes to run the modules and configure the nodes automatically without actually using the router CLIs.
Zabbix Monitoring Server
- Zabbix monitoring server will be configured in integration with ansible to monitor the health of the network and the traffic flow.
Deliverables
This project aims at delivering a working enterprise network deployed over GNS3 and automated using Ansible and Napalm automation tools. Also, deliver the health of the devices and traffic flow monitored using a monitoring server again automated using Ansible.
References
- Edelman, Jason, et al. Network Programmability and Automation: Skills for the Next-Generation Network Engineer, O’Reilly Media, Incorporated, 2018. ProQuest Ebook Central, http://ebookcentral.proquest.com/lib/rit/detail.action?docID=5261404.
- Juniper- https://www.juniper.net/us/en/products-services/what-is/network-automation/
- Reshma T.U. and James Komala. “Implementation of Internet Access in MPLS-VPN Technique on ISP.” i-Manager’s Journal on Wireless Communication Networks7.3 (2018): 38-45. ProQuest. Web. 13 Aug. 2019 https://search-proquest-com.ezproxy.rit.edu/docview/2222596785?pq-origsite=summon
- Phillips, C., et al. “Managing Dynamic Automated Communities with MPLS-Based VPNs.” BT Technology Journal 24.2 (2006): 79. ProQuest. Web. 13 Aug. 2019.https://search-proquest-com.ezproxy.rit.edu/docview/215203307?pq-origsite=summon
- Samll, S., et al. Scalable VPNs for the Global Information Grid, IEEE, 2005, doi:10.1109/MILCOM.2005.1605702.
- Jia, Yuxiao, et al. Dynamic Resource Allocation in QoS-enabled/MPLS Supported Virtual Private Networks and its Linux Based Implementation, vol. 3, IEEE, 2002, doi:10.1109/CCECE.2002.1012966.
- Slideshare- https://www.slideshare.net/apnic/mpls-l3-vpn-deployment
- Cisco- https://www.cisco.com/c/en/us/solutions/automation/network-automation.html
- Rosen E and Rekhter Y: ‘BGP/MPLS VPNs’ IETF RFC2547 (March 1999).
- Ansible- https://docs.ansible.com/ansible/latest/network/index.html
- Github- https://github.com/ktbyers/netmiko/blob/develop/README.md
- Github- https://ktbyers.github.io/netmiko/docs/netmiko/index.html
- Napalm- https://napalm-automation.net
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal



